Symmetric and Asymmetric Encryption

To keep it simple, let’s go back to the time of Roman Empire. Gaius Julius Caesar was a Roman general. He shared his important and sensitive information to other general in cipher text. He did not want his enemies to find out such information. Julius Caesar used the technique (known as Caesar cipher) where he left shifted the alphabet orders by 3. So, plain alphabet “A” become “D” in cipher. This is the key that he shared with someone he trusts. It was reasonable secure at that point of time.
That is one of the technique used long time ago. As the time goes by, the technology has evolved. With the help of modern computer, Caesar Cipher can be cracked in milliseconds. For example, English alphabets has 26 letters and it would only take at most 25 times to decrypt the data.
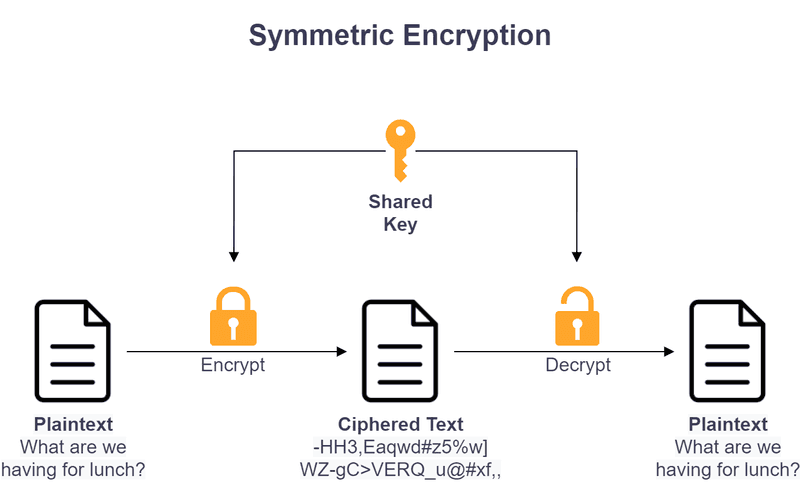
Symmetric Encryption
Symmetric encryption is a widely used encryption technique where one single shared key is used for both encrypting and decrypting information. The shared key is securely shared among different parties to perform encryption and decryption.
So great scientists and mathematicians have come up with more secure algorithms. The following are the widely used symmetric encryption algorithm:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- IDEA (International Data Encryption Algorithm)
- 3DES (Triple DES)
- RC4 (Rivest Cipher 4)
- RC5 (Rivest Cipher 5)
- RC6 (Rivest Cipher 6)
Summary
- Asymmetric encryption uses two mathematically linked keys, public key and private key
- Public key can be shared and private key cannot be shared
- For digital signature, private key is used to sign the message and public key is used to verify its authenticity
- More secure than symmetric encryption.
- Slower to execute than symmetric encryption due to the complex logic and mathematic involved
- Has longer key length. Recommended to be 2048 bits or greater
- More suitable for transmitting smaller data securely.
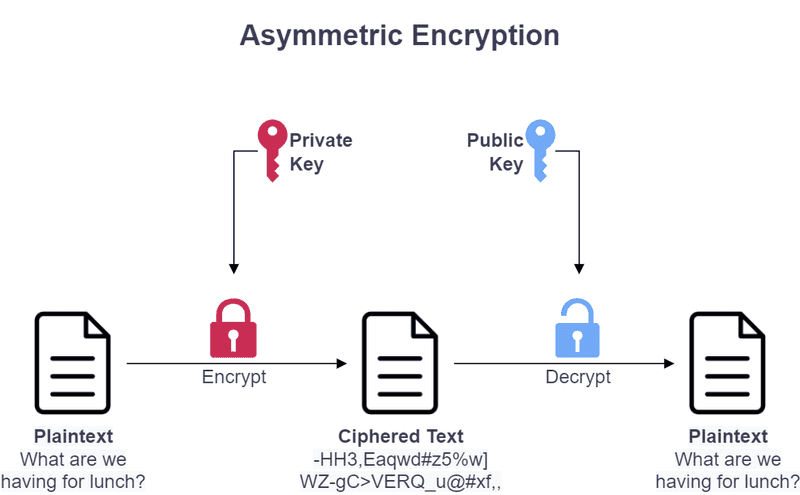
Asymmetric Encryption
Asymmetric encryption, also known as public key encryption, uses a set of public key and private key which are mathematically linked. Public key is shared publicly for encrypting data. Private key is kept in secret and cannot be share with anyone. It is used to decrypt data which are encrypted with its mathematically linked public key.
The following are the common asymmetric encryption algorithm:
- RSA (Rivest Shamir Adleman)
- ECC (Elliptical Curve Cryptography)
- ECDHE (Elliptic-curve Diffie–Hellman)
- DSA (Digital Signature Algorithm)
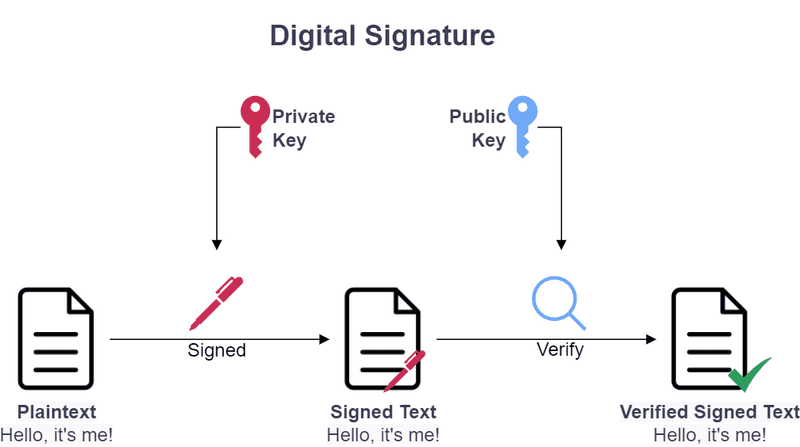
Digital Signature
Digital signature are also based on Public Key Infrastructure (PKI) and can be verified the authenticity of message. To explain more, sender can digitally signed messages or data with private keys. The messages are not not encrypted. Any receiver can verify that the message is actually sent from the sender by using sender’s public key. In other words, the message is not modified by third party or someone pretending to be the sender.
Summary
- Asymmetric encryption uses two mathematically linked keys, public key and private key
- Public key can be shared and private key cannot be shared
- For digital signature, private key is used to sign the message and public key is used to verify its authenticity
- More secure than symmetric encryption.
- Slower to execute than symmetric encryption due to the complex logic and mathematic involved
- Has longer key length. Recommended to be 2048 bits or greater
- More suitable for transmitting smaller data securely.
Conclusion
To conclude, I am not saying that one encryption technique is better than the other one. Everything has its own advantages and disadvantages. We can choose any encryption technique that is most suitable for our use cases and can gives us full benefits. It is not restricted to use only one technique but we can combine up to our imagination. Same with how Transport Layer Security (TLS) works. It uses asymmetric encryption to open up the connection between client and server. Then, transfers the symmetric encryption key using asymmetric encryption.